Secure Operations Center
Real-time visibility into an organization’s security posture
Single Point of Contact for Security-Related Events
Netcracker’s Security Operations Centers (SOCs) function as multipurpose command centers providing global security oversight. SOCs bring together industry-leading technologies in one place to protect applications and personal devices, control infrastructure access, continuously scan for breaches and vulnerabilities and proactively detect threats. With SOC locations in the Americas, EMEA and APAC, Netcracker is capable of operating around the clock, enabling a true follow-the-sun approach to rapidly mitigate emerging threats. SOC locations are also reinforced with state-of-the-art capabilities that allow Netcracker’s security experts to offer End-to-End Monitoring and Threat Detection and Response services.
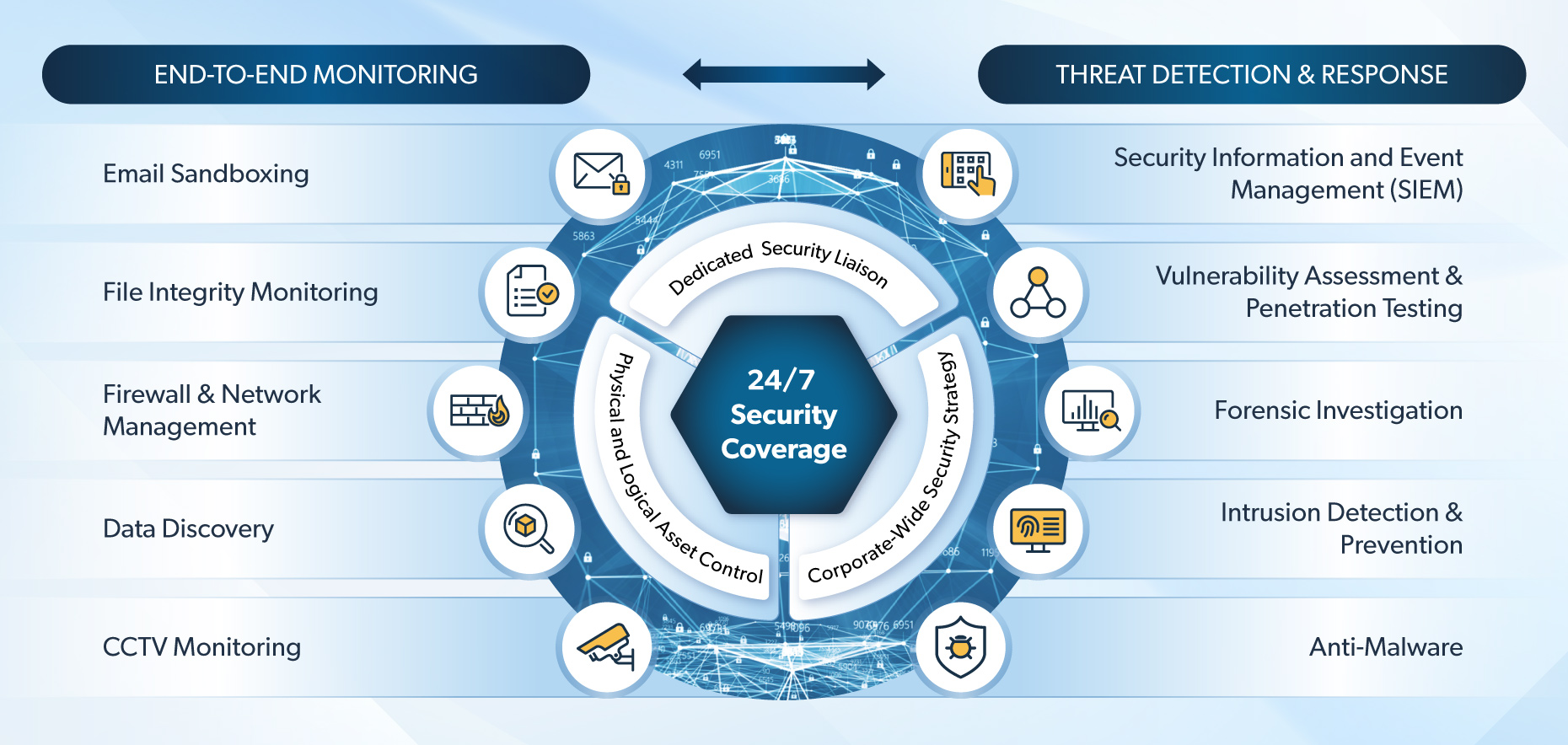
End-to-End Monitoring services deliver complete visibility across the entire security landscape, integrating cyber and physical safeguards into a unified view. Netcracker detects insider threats and compromised accounts within a customer’s environment, identifying malicious actions before they escalate. Both the perimeter and internal traffic flows are monitored to detect intrusion attempts, data exfiltration and other suspicious network activity in real time. Through advanced data discovery, Netcracker locates and classifies sensitive information across on-premises, cloud and endpoint environments, giving essential context to monitoring and enabling risk-based prioritization. Bridging the gap between cyber and physical security, CCTV and access control monitoring detect unauthorized physical entry that could lead to digital threats. This holistic approach ensures nothing goes unnoticed – from the data center floor to the farthest endpoint.
Threat Detection and Response services provide comprehensive protection against evolving cyber risks by combining advanced analytics and remediation capabilities. Netcracker aggregates logs from multiple systems, correlates events and applies powerful analytics to identify suspicious patterns across the entire environment. Proactive vulnerability assessments generate prioritized remediation plans, enabling teams to patch or harden systems before attackers can exploit weaknesses. In the event of an incident, Netcracker conducts a deep forensic investigation to uncover the root cause and provide evidence-based strategies for containment and recovery. The intrusion detection and prevention systems continuously monitor network and system activity for signs of malicious behavior or policy violations, while anti-malware solutions scan, identify and neutralize both known and emerging threats on endpoints, servers and gateways. This end-to-end approach ensures rapid threat identification, effective response and long-term resilience for customers.



